Setup Single Sign On with AAD using SimpleSAMLphp
This blog provides step-by-step instruction on how to setup Single Sign On with Azure AD using SimpleSMPLphp API (apply to MediaWiki site as an example).
Install and configure SimpleSAMLphp
-
To download SimpleSAMLphp, https://simplesamlphp.org/download , extract the download to wwwroot/simplesamlphp
-
Configure admin: Edit wwwroot/simplesamlphp/config/config.php,
- Modify baseurlpath: ’baseurlpath’ => ‘simplesamlphp/www/’
-
Set admin login passwoed: ’auth.adminpassword’ => ‘<your-admin-password>’
-
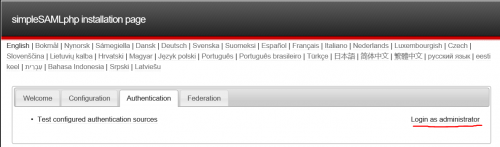
Browse to simplasamlphp admin page, <your-site-url>/simplesamlphp/www/, login with ‘admin’ and the password you set in config.php
-
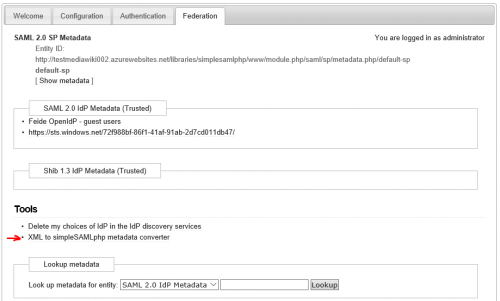
Generate metadata in XML: Click Federation tab, choose “XML to simpleSAMLphp metadata converter,
- Copy raw XML from https://login.windows.net/72f988bf-86f1-41af-91ab-2d7cd011db47/FederationMetadata/2007-06/FederationMetadata.xml
paste to “XML metadata” area, and click “Parse”, you will see the PHP code populated in “Converted metadata” area.
- Copy the PHP code into wwwroot/simplesamlphp/metadata/saml20-idp-remote.php
-
Configure authsources: Add following PHP code in wwwroot/simplesamlphp/config/authsources.php:
Find $config = array( 'default-sp' => array(...), );Add the code:
'idp' => 'https://sts.windows.net/72f988bf-86f1-41af-91ab-2d7cd011db47/', -
Check the default settings for php sessions, if session.phpsession.cookiename is ‘null’, set it to ‘PHPSESSID’.
Integrate with MediaWiki site
- Download SimpleSamlAuth extension from https://github.com/jornane/mwSimpleSamlAuth/releases , extract to wwwroot/extensions/SimpleSamlAuth
-
Modify LocalSettings.php to require authentication:
require_once "$IP/extensions/mwSimpleSamlAuth/SimpleSamlAuth.php"; $wgSamlRequirement = SAML_REQUIRED; $wgSamlCreateUser = true; $wgSamlUsernameAttr = '[http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name'](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name'); $wgSamlRealnameAttr = '[http://schemas.microsoft.com/identity/claims/displayname'](http://schemas.microsoft.com/identity/claims/displayname'); $wgSamlMailAttr = '[http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name'](http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name'); $wgSamlSspRoot = '/libraries/simplesamlphp'; $wgSamlAuthSource = 'default-sp'; $wgSamlPostLogoutRedirect = NULL;
Configure authentication in Azure AD
- In Azure management portal (classic), select Active Directory from menu, choose Microsoft tenant
- Select Application tab, Add your application
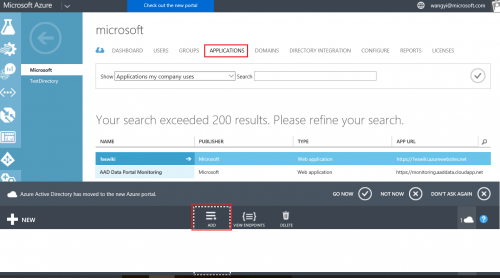
- Select a name for your application, keep “Web application and/or web API”, click next
- In “Sign on URL”, use home url of your site, for “App ID URL”, use the URL to default-sp, e.g. http://<your-site-url>/libraries/simplesamlphp/www/module.php/saml/sp/metadata.php/default-sp
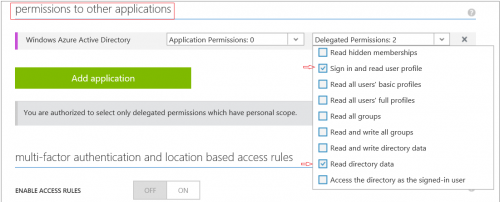
- From Configure tab of your application, find “permission to other applications” section, check Enable “sign in and read users’ profiles” and “read directory data” under Delegated Permission,save the change.
References: